In this article, we will learn the pros and cons of using Face Recognition as an authentication method. We will also see how it can be spoofed and the methods that can be used to detect the spoofing ...
Latest From the Blog
DepthAI Pipeline Overview: Creating a Complex Pipeline
May 17, 2022 3 Comments 15 min read
Share
By 3 Comments
TensorFlow Lite Model Maker: Create Models for On-Device Machine Learning
May 10, 2022 4 Comments 14 min read
Share
CNN Deep Learning Edge Devices Image Classification Model Optimization OpenCV Tutorials Post Training Quantization Raspberry Pi
By 4 Comments
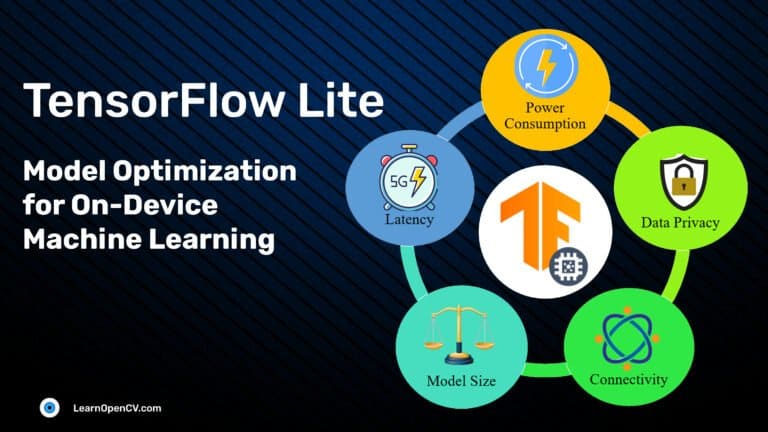
TensorFlow Lite: TFLite Model Optimization for On-Device Machine Learning
May 3, 2022 4 Comments 14 min read
Share
CNN Deep Learning Edge Devices Image Classification Model Optimization OpenCV Tutorials Post Training Quantization Raspberry Pi
By 4 Comments
Object Detection With Depth Measurement Using Pre-trained Models With OAK-D
April 26, 2022 5 Comments 12 min read
Share
By 5 Comments
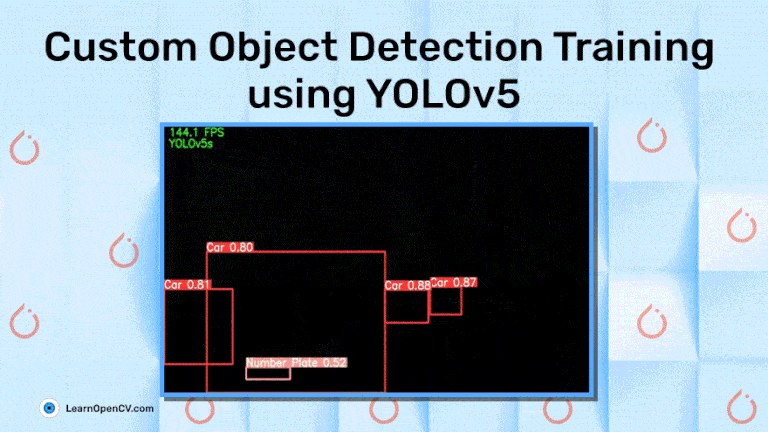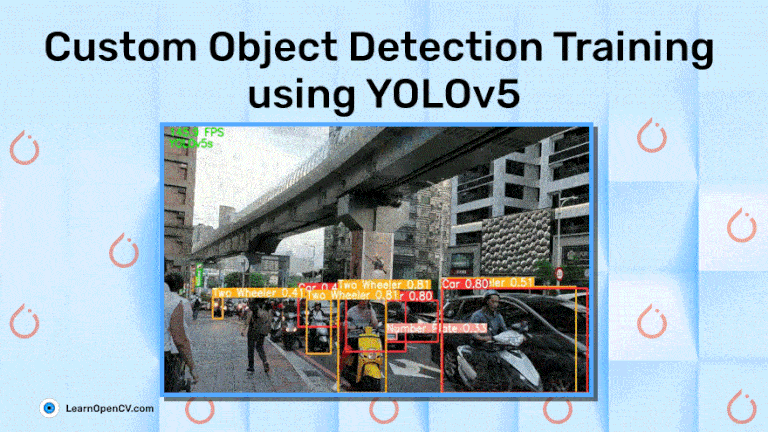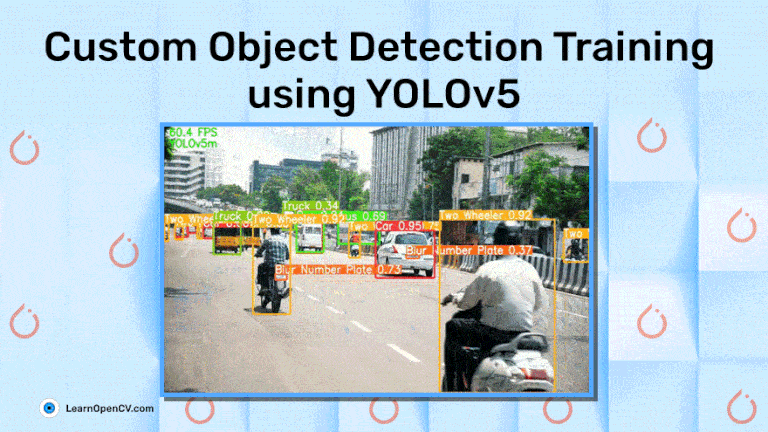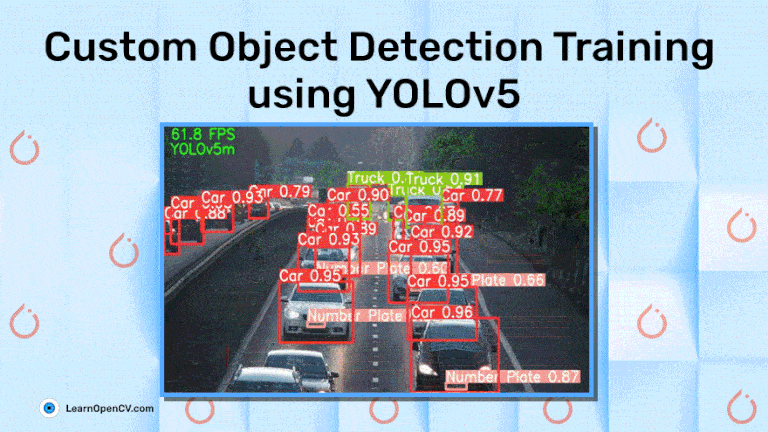
YOLOv5: Expert Guide to Custom Object Detection Training
April 19, 2022 2 Comments 27 min read
Share
By 2 Comments
- « Go to Previous Page
- Page 1
- Interim pages omitted …
- Page 37
- Page 38
- Page 39
- Page 40
- Page 41
- Interim pages omitted …
- Page 83
- Go to Next Page »